What Is Layer 2 Forwarding (L2F), & How It Works?
This post will explain what is layer 2 forwarding l2f. The Layer 2 Forwarding protocol is a media independent innovation established at Cisco Systems. It’s a media-independent tunneling procedure that came to life at the first Virtual Private Networks advancement stages. It allows for Virtual Private Networks to exist over a public network by turning data-link layer packages in web protocols like SLIP (Serial Line Web Protocol) or PPP (Point-to-Point Protocol).
Servers can make the most of L2F for things such as user authentication through vibrant address allotment, Quality of Service (QoS) and Remote Authentication Dial-In User Service. Cisco’s Internetwork operating system enforces L2F in routers also.
What Is Layer 2 Forwarding (L2F), & How It Works?
In this article, you can know about what is layer 2 forwarding l2f here are the details below;
The tunneling method to developing personal networks is independent of the Internet Protocol (IP). Thus, the exact same innovation can develop secure tunnels in other network contexts like ATMs or Frame Relay.
The L2F protocol: How does it work?
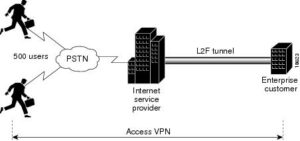
Let’s take the PPP procedure. It connects a dial up client with the NAS (short form of network access server) when it receives the call utilizing Layer 2 Forwarding. Also check how to fix regarding discord javascript error
Client-triggered PPP connections get ended at a PPP service supplier’s NAS (Network Access Server)– this is normally an ISP (Internet Service Provider). L2F enables the customer to connect beyond the Network Access Server to a remote node. That system enables the client to act as if it was directly linked to that remote node instead of linking to the NAS. Within the L2F world, the NAS has only one job just to exchange forward frames from the client all the way to the far-off node.
The crucial thing to bear in mind is that Cisco’s L2F protocol can undoubtedly work over the IP procedure, however it doesn’t really need it. It can work in addition to other protocols as it is. For example, it often works when used in tandem with VDU (Virtual Dial-Up).
Authentication types
L2F authenticates remote users using PPP along with other authentication systems that can consist of Terminal Access Controller Access Control System & Remote Authentication Dial-In User Service (RADIUS).
– There are a number of connections in L2F tunneling channels, which is among the reasons they’re different from PPTP tunneling channels.
– The authentication occurs in 2 stages. The ISP performs the very first one before the tunnel shows. The tunnel comes alive in the gateway in the 2nd stage upon the connection getting online.
– The SP and the specific corporate company gateway utilize an agreed-upon authentication procedure before allowing the tunnel in between the remote and local networks to exist.
– The L2 works on the information connection layer (or that’s the word in the OSI recommendation documentation). It therefore makes it possible for users like NetBEUI or 1PX instead of IP such as PPTP.
PAP– Password Authentication Protocol
First, the client and the server connect. Then the client sends a bundle with the user’s qualifications (password and username). Then the server will give or refuse a connection request, depending upon its ability to verify the request, which can be rejected or confirmed.
CHAP– Challenge Handshake Authentication Protocol
This procedure takes a various approach to the authentication process. Here, the customer keeps sending the server an authentication packet regularly. The customer and the server keep exchanging these CHAP packages regularly to validate the user’s credentials at both ends. As long as the authentication stays legitimate, the connection keeps online. Also check msmg toolkit
L2F’s pros
– It guarantees transmission security, producing an end-to-end secure tunnel for data encapsulation.
– It can improve the security of other protocols.
– It supports user authentication for other procedures such as RADIUS, QoS, and Dynamic Address Allocation.
– The L2F tunnels support multiple connections.
L2F’s cons
– Personal privacy security in L2F relies on the protocol’s capability to tunnel the information instead of providing encryption.
– The protocol lacks data flow control.
– This protocol doesn’t boast AV (Attribute-value) set hiding.
Introduction of L2F protocol security
The virtual dial-up service initiates. Then the ISP will pursue authentication. The ISP appreciates two things just: the user’s identity and the home gateway they wish to reach. So it attempts to discover both things as the call can be found in. As soon as those two bits of details emerge, it starts linking to the preferred home entrance, based upon the authentication data gathered. The last touch occurs at the house entrance, which accepts or declines the connection.
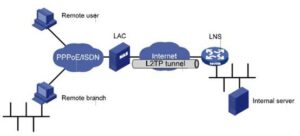
The home gateway has an extra task to do. It needs to protect the connection versus 3rd parties (snoopers, hackers, governments) to develop tunnels to the house gateway, obstruct the present tunnel or pirate it.
The tunnel creation requires an authentication process between the ISP and the home entrance. This is the authentication bit that safeguards the tunnel against harmful attacks. And this is the reason L2F is so crucial. It may not be apparent from these details. Still, the reality is that these authentication procedures can end up being safer if you can make the most of a number of protocols concurrently to secure them. And L2F gives us that opportunity, and it can work together with several protocols. Thus it makes the authentication processes fast and much safer. And its combination with them is smooth.
Conclude
Let us compliment you on your interest in some of the aspects of digital innovation and privacy. L2F is such a basic procedure in the digital world that you will never ever notice it’s there– until it’s not. That’s how these things work.
When Cisco & Microsoft merged in 1999, L2F ended up being the Layer 2 Tunneling procedure. It’s still around, and you’re probably utilizing everything the time without noticing it.
If you utilize a VPN service, then L2F is right at the heart of the service. That’s because it’s the important things that creates the end-to-end tunnel of encapsulated information that permits your traffic to walk around the Web safely away from the spying eyes of those third parties you’re keen to avoid. And it’s so essential and so subtle that it’s hardly ever discussed clearly (it’s OpenVPN and similar procedures that get all the limelight). But it’s however there, making whatever possible.
L2F has a fundamental constraint that makes it a bit less attractive than others: it lacks file encryption. Yes, the tunnel is safe but not encrypted, which’s a big problem in this day. If the tunnel falls to a breaking, then the data in the tunnel is available for anybody to check out. Also check vac was unable to verify
L2F needs to benefit from another procedure that can offer file encryption, hence making the tunnel foolproof. Then, the tunnel provides versatility and information stability, while the 2nd protocol (GRE, TCP) secures the information stream.
now you know all you need to understand about L2F.this is not the type of digital innovation that you will be fiddling with on your phone or laptop computer unless you’re a sys-admin at an ISP. Other types of users wouldn’t make the effort to read this short article and check out protocols. However you understand that this type of details puts you ahead of the pack and will give you the best weapons to protect your privacy. That’s why we began by congratulating you on reading this. After all, having this details and utilizing it to your advantage is what being Privacy Savvy is everything about!